It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.” – Warren Buffett
Many reputations and enterprise brands are currently at risk. An enterprise’s brand reputation consists of various factors. A strong brand will endure criticism, and since all consumer experiences are subjective, no brand can get everything right, all the time.
And that's where you come in, as enterprise security, whether it’s done well or not, can significantly impact an enterprise’s brand.
This year’s Security 500 report offers 10 security risks to your enterprise’s reputation, as ranked by you in your Security 500 survey responses, in addition to how one CSO is mitigating them in his enterprise.
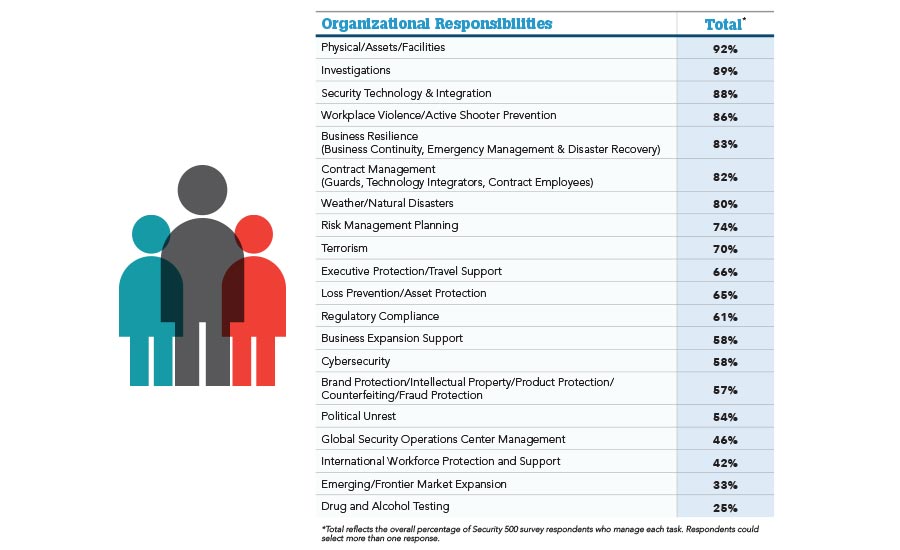
R. David (Dave) Mahon is the Chief Security Officer at CenturyLink, a role that he’s held since April 2011. As CSO for the third-largest communications provider in the U.S., his responsibilities include enterprise-wide security strategy, information security, cyber defense, critical infrastructure protection, physical security, network fraud and abuse, industrial security, international travel security, threat intelligence, workplace violence prevention, executive protection and investigations, and he is also the company’s liaison with the National Security Telecommunications Advisory Council (NSTAC), National Cybersecurity and Communications Integration Center (NCCIC), as well as federal and state law enforcement and homeland security agencies.
Trend 1: Workplace Violence and Active Shooter
Once again this year, Security 500 members rated workplace violence and active shooter as the top number one threat facing an enterprise and its security team.
As of this writing, an investigation continues as to why Stephen Paddock shot and killed 59 people and wounded 489 at the Mandalay Bay in Las Vegas. It remains to be seen how deeply the casino and resort’s reputation has been affected after the tragedy, and how that will impact its future prospects and its bottom line.
Workplace violence takes many different shapes and forms, ranging from theft or the threat of violence to shootings and murder. Despite the amount of time spent studying the incidents, workplace violence remains extremely difficult to mitigate, even for experts.
About two million workers a year are affected by some form of workplace violence, according to OSHA, which includes everything from verbal abuse to physical assaults to homicide. The most extreme types of violence result in fatalities. Between 1992 and 2012, there were 14,770 workplace homicide victims, or roughly 700 a year on average, according to federal government statistics.
At CenturyLink, Mahon has had a workplace violence prevention program for more than 10 years. It includes an active shooter program for its 40,000 people, approximately 20,000 contractors and 3,000 vendors.
Mahon uses data from OSHA reports and other mental health industry studies to ensure CenturyLink’s workplace violence mitigation strategy is working effectively. “We also train our employees about our code of conduct and what is acceptable behavior,” he says. “And we look for evolving indicators of workplace violence. The vast majority of the time, people just don’t go postal or ballistic. Their behavior evolves through a defined cycle, and it continues to escalate when it’s not addressed.”
Therefore, the CenturyLink program includes a threat assessment team that includes professionals with backgrounds in mental health, legal, healthcare and training, and specific plans on how to identify and mitigate workplace violence situations.
Trend 2: Cybersecurity
According to a recent Nationwide Insurance survey, nearly half of business owners have been victims of cyberattacks, and didn’t know it. Nationwide’s annual survey of business owners found that 13 percent said they experienced a cyberattack. However, that number jumped to 58 percent of owners who identified as victims when shown a list of the following types of attacks – a 45-percent gap and lack of understanding about what constitutes an actual attack.
The survey also found that more than 20 percent of cyberattack victims spent at least $50,000 and took longer than six months to recover. But seven percent spent more than $100,000, and five percent took a year or longer to rebuild their reputation and customer trust. “Cyberattacks are one of the greatest threats to the modern company,” says Mark Berven, president of Property & Casualty for Nationwide. “Business owners are telling us that cybercriminals aren’t just attacking large corporations on Wall Street. They’re also targeting smaller companies on Main Street that often have fewer defense mechanisms in place, less available capital to re-invest in new systems and less name recognition to rebuild a damaged reputation.”
Part of the problem facing a business’s ability to recover from an attack is not being prepared. Many enterprises still don’t have a cyberattack response plan in place, or a plan in place to protect employee data, or a plan to protect customer data. Additionally, the threat continues to grow as more companies are now frequently using new technologies in a potentially unprotected environment, including the Internet of Things and Artificial Intelligence.
At CenturyLink, Mahon has an Insider Threat Program as a part of the cybersecurity risk mitigation plan. “From an insider cybersecurity threat perspective, people just don’t go ballistic from the cybersecurity side,” Mahon says. “They demonstrate concerning behavior. But if you don’t train your employees, then they don’t know how to identify concerning behavior and where to report it.”
“Insider threat to cybersecurity has really three components,” Mahon says. “First, 90 to 95 percent of the problem is hard-working people are trying to do the right thing every day. Yet, they click on the wrong email. It still causes the breach. So you have to train your employees on good cyber hygiene. Then there is the malicious insider, which is a very small percentage of employees. But because they have authorized access and some knowledge of your vulnerabilities, their ability to cause substantial damage is significant. And in the middle of those two groups is what we call the fence sitter, meaning you acquire a company, and they do not think the rules apply to them. They’re not necessarily trying to do anything wrong, but they’re not behaving in a manner consistent with good cyber hygiene.”
“We also see an evolution in the industry that’s really not cybersecurity anymore,” Mahon says. “If you think about where this industry began 25 years ago, we called ourselves IT security, meaning there was a server with an anti-virus [solution] on it. That was the sum total of it – technical solution-based thinking to the threat. We then changed the name of our profession to information security and deployed defense in depth, which is a typical mindset but doesn’t recognize as a technical solution-based thinker that you have to have an intense focus on the threat. And then we shifted our profession’s name to cybersecurity because we recognized it’s more of an ecosystem that’s at risk. But really, the term should be cyber risk management. You have to understand how to design and implement a risk management program from a threat-focused approach to the adversaries you are facing, and then develop and implement a roadmap that your board of directors can understand and support.”
Trend 3: Terrorism
Explosives. Arson. Guns. Driving into a crowd of people. These are the most common tools that terrorists use to inflict fear and destruction on the public, according to Dr. Robert Tessler of the Harborview Injury Prevention and Research Center in Seattle, who created the Global Terrorism Database based on work at the National Consortium for the Study of Terrorism and Responses to Terrorism at the University of Maryland. The report defines a terrorist attack as the “use of illegal force and violence by a non-state actor to attain a political, economic, religious or social goal through fear, coercion or intimidation.”
The data was from 2,817 terrorist attacks in the United States, Canada, Western Europe, Australia and New Zealand between 2002 and 2016. Of these, 85.3 percent were in Western Europe, and 11.7 percent were in the U.S. Explosives were used in 49 percent of all attacks, followed by arson (36 percent), firearms (9.2 percent) and vehicles that plowed into crowds of people (5.4 percent).
Terrorism, in its many forms, is threat number three to an enterprise’s security program, according to Security 500 member responses.
To mitigate terrorist threats at CenturyLink, Mahon examines the enterprise’s global footprint. “We study all the adversaries that are out there and we divide them into five categories: nation-state (Chinese, Russians, Iranians, etc.), multinational criminal organizations, terrorists, hacktivists and insiders. Terrorism can include both a cyberterrorist attack and a physical terrorist attack.”
Trend 4: Budget and Funding
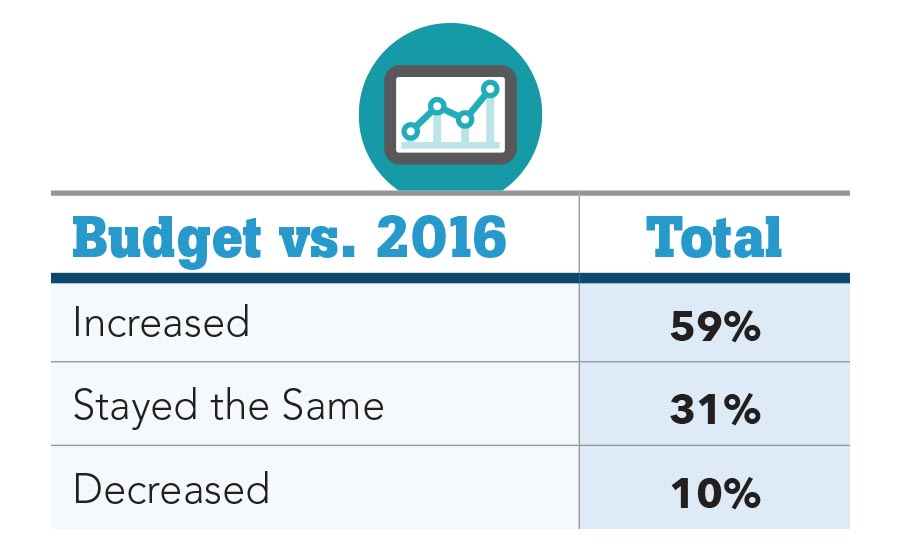
On the heels of mitigating terrorism is the challenge to secure the funding to do so. This year, 59 percent of Security 500 survey respondents reported a budget increase, while 31 percent reported their budgets stayed the same from 2016 and 10 percent reported a budget decrease. Any type of budget decreases, of course, makes it difficult to continue to mitigate security risks and protect the enterprise’s brand and reputation. When security budgets do increase, the argument can be made that it’s because organizations and the C-suites understand and embrace security’s role and success in mitigating risks, which are illustrated via metrics and measures.
At CenturyLink, Mahon and his team develop the security budget to ensure his CEO, board of directors and other leaders are aware of the risks to create a risk profile for the company. “That begins to drive your programs and your budget,” he says. “What problem are you trying to solve? What’s the objective? What’s the solution? And what’s the roadmap? From there, you build business cases. In cybersecurity for this year I have 10 initiatives that are part of a three- to four-year roadmap that I explain to my CFO.”
Trend 5: Geopolitical and Protests
Political protests have increasingly become abundant in America. A recent analysis by economists from Harvard University and Stockholm University finds that protests do have a major influence on politics, just not in the way you might think. Their research shows that protests work not because big crowds send a signal to policy-makers, but rather because protests get people politically activated.
Whether they work or not, the challenge for enterprise security is when they turn up on your door, such as when Greenpeace protesters infiltrated Procter & Gamble headquarters in Cincinnati and hung up large banners from the two towers there in 2014, or when protestors showed up at McDonald’s annual shareholder meeting in downtown Chicago earlier this year to protest against low wages. It’s a security director’s worst nightmare, but it also can be an opportunity to allow security to get the visibility it needs to effect the changes that are necessary to protect the company and the brand.
“You can either be a direct target of a protest, or you can be an indirect bystander target. Either way, you have problems,” Mahon says. CenturyLink has a global threat intelligence program led by a chief intelligence analyst who examines geopolitical risks and maps people, processes and technologies across the globe, including global adversaries.
It’s a constant process of measuring country risks and asking how those risks will affect our investment and presence in that country,” he says.
Part of that assessment includes monitoring social media, which is more commonplace these days. Mahon and his team proactively examine social media sites to view how political points of view and issues are evolving in areas where CenturyLink operates.
Trend 6: Business Continuity
In the past few months, Hurricane Harvey destroyed parts of Houston and its surrounding suburbs, Hurricane Irma hit Florida, and parts of Northern California were destroyed by fire. Globally, other natural disasters including flooding and monsoons in south Asia, landslides and drought in Africa, earthquakes in Mexico and more. And you should be planning for the next natural disaster.
About one-third of organizations see Hurricanes Harvey and Irma, Typhoon Hato, the earthquakes in Mexico and other disasters as catalysts to reevaluate their emergency planning, according to a poll taken during a recent Marsh webcast. However, one third said they were not sure if this year’s series of disasters would be enough to spur such measures.
When asked which area related to catastrophe planning would their enterprise most benefit from spending time and resources in the next two years, 37 percent said insurance coverage evaluation relative to risks, 22 percent said supply chain resiliency, 20 percent said personnel preparation, 16 percent said catastrophe modeling, 15 percent responded risk interdependencies/interrelatedness, and 12 percent said risk bearing capacity. Overall, Security 500 respondents, who ranked business continuity as trend number six, continue to make business continuity plans a major priority.
CenturyLink operates a number of SOCs for cybersecurity and physical security, in addition to a business continuity plan to support the enterprise. Mahon adds, “I have a team member assigned to the U.S. Department of Homeland Security Cybersecurity and Communications Integration Center and National Coordinating Center, to assist with our business continuity implementation. If there’s a major threat from a cyber perspective, or a threat from a natural disaster, we’re sitting in the command center. We assist the federal government with their business continuity plans (BCP). With a natural disaster, we have to protect our own buildings and our people. But we’re also responsible for our networks. So much of our BCP is ensuring that our networks are operating during and after a natural disaster, ensuring that telecommunication vaults and fiber in the ground haven’t been damaged, and if they are, to quickly restore them.”
Trend 7: Staffing
Security 500 survey respondents rate staffing, for both cyber and physical security, as the number seven trend this year.
By 2022, the global cybersecurity workforce will be short by around 1.8 million people, according to the Global Information Security Workforce Study (GISWS) by Frost & Sullivan.
But many programs are popping up to close that gap and to train future security leaders, including at Sentara Healthcare, which recently created the Cyber Student Staffing Program to recruit students in its home state of Virginia to be future cybersecurity workers. In addition, there’s the Centers of Academic Excellence in Cybersecurity program, which is jointly sponsored by the National Security Agency (NSA) and DHS. The goal of the program, as stated by the NSA, is to reduce vulnerability in our national information infrastructure by promoting higher education and research in cyber defense and producing professionals with cyber defense expertise for the nation. There are currently more than 200 higher education institutions, universities and colleges that participate in the program.
At CenturyLink, Mahon says, “One of the first things you have to recognize about employee training is employees are generally trying to do the right thing. But if you don’t first answer the why for them, they will ignore the training and ignore what they should be doing.”
CenturyLink’s annual information security awareness training program incorporates information about the company’s digital transformation strategy, how enterprise security enhances the customer experience, and what each employee can do to support those efforts.
Trend 8: Theft and Investigations
Six weeks. That’s how long it took for Equifax to notify its customers that their data was breached. The breach began in May, was discovered in July, and the company claims that the time between the discovery and the public disclosure was spent investigating the attack. However, that excuse holds little weight to the public, which has seen few tangible results from the internal investigation. Without frank and forthright communication from the security team at Equifax explaining how the breach occurred and what they were doing to remediate the issue, the public remains confused, and the company missed an opportunity to salvage their reputation.
Ninety-two percent of Security 500 survey respondents this year report having responsibility over theft and investigations in their enterprise. That number has been consistently that high since Security magazine began publishing the Security 500 report more than 10 years ago.
At CenturyLink, Mahon is mitigating theft from the 15,000 trucks in the company’s fleet, in addition to huge garages, large yards of fiber and other construction materials. He’s also continuing to work to mitigate copper theft, by working with federal investigative teams.
“But we also try and solve the problem more systemically, he says. “When we see a cable theft in an area where gangs are prevalent, red flags are raised. We examine how those individuals not only commit the crime but how they monetize it. We want to take away the ways for them to make money. So, how do they steal from us and then sell it to the salvage yards? We work with state legislatures to promote legislation that does not allow the salvage industry to take copper cable that has any markings indicating it’s from a telecommunications company. We’ve also testified at the federal level in Congress on these types of legislation.”
Trend 9: New and Emerging Technologies
Many Security 500 members have just returned from the recent ASIS International in Dallas, where you likely saw hundreds of new security technologies and sales people lined up in trade booths that were willing to sell you the latest and greatest. This trend of keeping up with new and emerging technologies shows up on the Security 500 survey each year. This year, again, 88 percent of Security 500 members reported responsibility over technology integration and maintenance within their enterprise.
At CenturyLink, Mahon isn’t considering using drones or robotics, at least for now. “But we are looking to automate many functions with card access, video and our guard services,” he says. “Within our cybersecurity space, for example, how do you profile network devices to understand their baseline behavior? How do you track anomalies to that behavior? And how do you link that behavior to other needs? How do we ‘self-heal,’ if possible? Some of this technology we have to build ourselves,” he notes. “In cybersecurity, we’re not finding vendor solutions that are leaps and bounds above other technologies. When we want enhancements, we bring vendors into our sandbox and advise them what we need from them.
“I’m fortunate to have on my team a CISO, Director of Cyber Defense, Director of Industrial Security, a Director of Critical Infrastructure Protection and Law Enforcement Liaison, a Director of National Security, and a Director of Fraud Management. So we do everything in the CSO office. We think that the biggest weakness in this industry, particularly with cybersecurity, is that we don’t develop a global security strategy to enable the achievement of your corporate objectives. Our global strategy is to consume security like you consume your healthcare, in a hospital. I’m the hospital administrator. I run the hospital, but I don’t own every department in the hospital. I bring in partners for different departments where I think it’s appropriate. That way I know exactly what my risks are.”
Mahon adds, “People think that physical security is separate from cybersecurity. It is not. In a security audit, it doesn’t matter whether you’ve failed the physical or the logical control. You still failed.”
Trend 10: Business Expansion
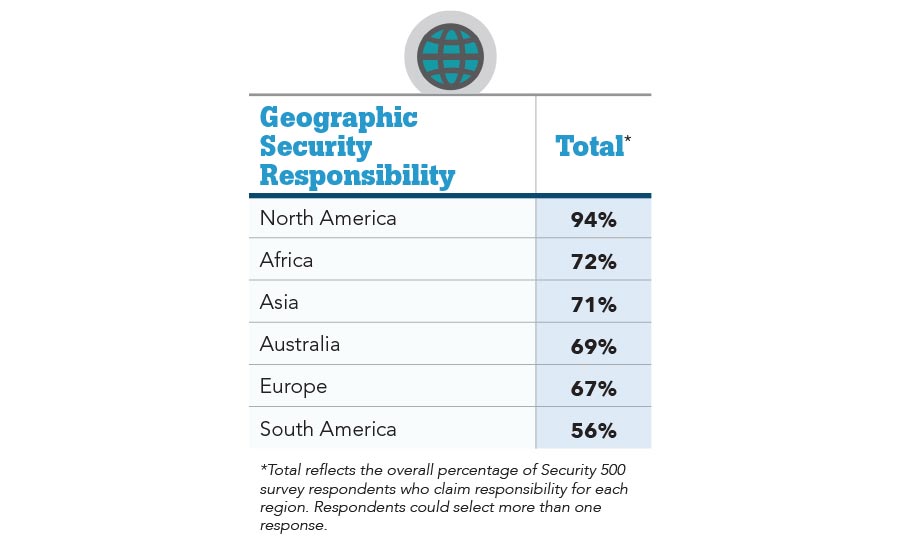
Again this year, Security 500 survey members reported increased responsibility for their enterprise’s operations in Asia, South America, Africa, Europe and Australia. In Australia, responsibility increased three percent; responsibility increased eight percent in Asia and six percent in South America. And with that comes risk to the enterprise brand.
From this year’s Security 500 profiles, enterprise security is essential to a brand’s success in business expansion and emerging markets.
For example, at Oracle, Mike Maloof, Vice President of Global Security, says his biggest challenge comes from the sheer size of the company and the fact that it’s on a global level. “Being in the IT sector, we’re not bound by your traditional supply chains and brick and mortar locations,” he says. “Given the fact that Oracle can be truly anywhere, whether that’s within a client organization or within an Oracle organization, we’re constantly assessing any potential risk to our organization.”
Brad Minnis, Senior Director, Corporate Safety and Security for Juniper Networks, is employing global best practices around supply chain processes, including technology features, to prevent the infiltration of counterfeit components into its supply chain, and to make it very difficult for people to counterfeit its products. For more on how enterprise security is enabling business expansion, check out the Security 500 Thought Leader Profiles, beginning on page 51 of this issue.







