ISC West 2023 product preview
ISC West 2023 is approaching, and with it comes the opening of the show floor. This year, security leaders can experience a number of cutting-edge security technologies, including automated anomaly detection in video surveillance, remote programming for doors, power distribution for security systems and more.
From robotic visitor management to mobile access control credentials, Security magazine spotlights solutions from companies at ISC West 2023.
Active Intelligence
Detects anomalous events in surveillance feeds
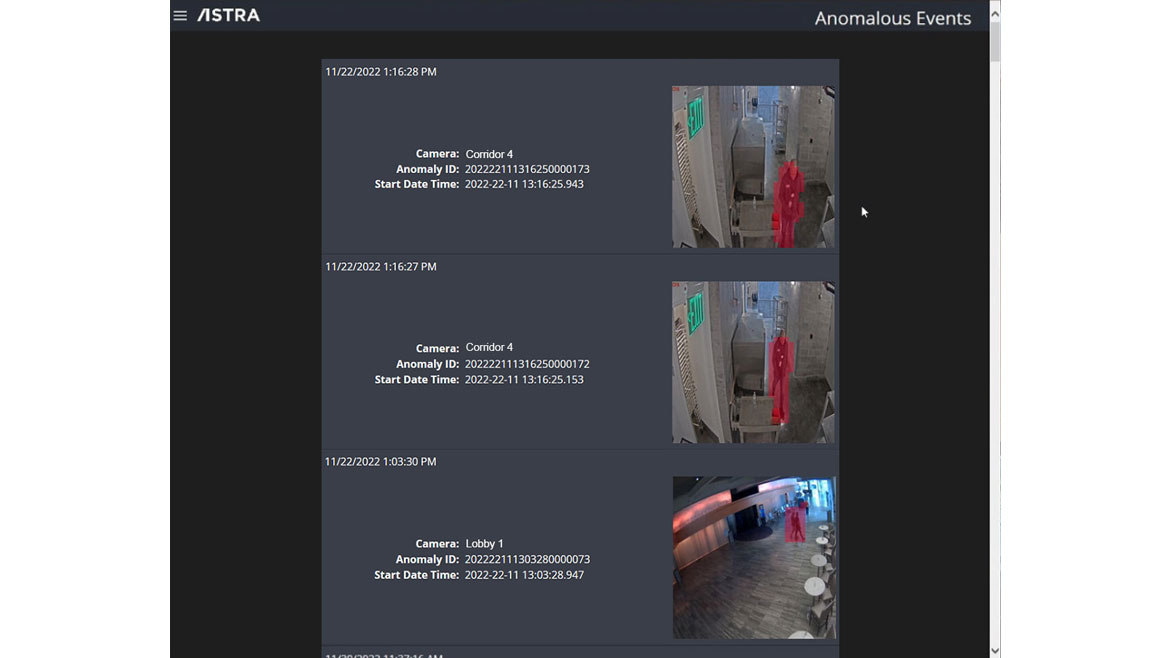 Astra is active intelligence’s anomaly detection solution designed to transform video security from a forensic investigation tool to a real-time threat prevention tool. The solution identifies anomalies within video surveillance feeds and integrates with a number of video management system (VMS) platforms. Running on hardware, Astra can put virtual eyes on video feeds and alert operators as soon as an anomaly is detected. The anomaly detection engine continues to learn and improve its performance using statistical analysis to identify anomalies in real time. Astra adapts to gradual scene changes like seasons, weather, traffic flow and schedule changes. Image courtesy of Active Intelligence
Astra is active intelligence’s anomaly detection solution designed to transform video security from a forensic investigation tool to a real-time threat prevention tool. The solution identifies anomalies within video surveillance feeds and integrates with a number of video management system (VMS) platforms. Running on hardware, Astra can put virtual eyes on video feeds and alert operators as soon as an anomaly is detected. The anomaly detection engine continues to learn and improve its performance using statistical analysis to identify anomalies in real time. Astra adapts to gradual scene changes like seasons, weather, traffic flow and schedule changes. Image courtesy of Active Intelligence
Find out more at www.activeintelligencecorp.com
Aiphone
Helps installers remotely program intercom systems

Aiphone’s Remote Programming Service for its IX series systems aim to help installers build, edit and save programming files within the Quikspec online design tool. A built-in programming wizard offers guidance with creating and modifying system, station and network settings to produce a downloadable programming file. Using the Remote Programming Service, installers can remotely set up and download multiple system preferences prior to arriving on a job site for installation. Available settings include enabling door release, adjusting station visibility with other stations, adding stations to a call list, selecting volume controls and more. Image courtesy of Aiphone
Find out more at www.aiphone.com
Altronix
Distributes power for access control technology
 With Altronix’s Trove2M2R solution, altronix power distribution combines with Mercury platform access controllers to support up to eight doors with power from a single 2U enclosure. This high-capacity rack mount drawer allows for installation, service and maintenance where wall space may be limited or not an option. Trove2M2R is customizable and available in pre-configured kits with power and sub-assemblies pre-wired and installed. All units include a 2U rack drawer with backplane, cam lock, tamper switch, as well as integrated Z-bracket to facilitate external wiring. Image courtesy of Altronix
With Altronix’s Trove2M2R solution, altronix power distribution combines with Mercury platform access controllers to support up to eight doors with power from a single 2U enclosure. This high-capacity rack mount drawer allows for installation, service and maintenance where wall space may be limited or not an option. Trove2M2R is customizable and available in pre-configured kits with power and sub-assemblies pre-wired and installed. All units include a 2U rack drawer with backplane, cam lock, tamper switch, as well as integrated Z-bracket to facilitate external wiring. Image courtesy of Altronix
Find out more at www.altronix.com
Boon Edam
Prevents piggybacking in access turnstiles
BE Secure, a secure overhead detection system from Boon Edam, Inc., for use with Turnlock Full Height Turnstiles aims to detect and prevent piggybacking within Boon Edam’s range of full-height turnstiles. Boon Edam’s Turnlock 150 Full Height Turnstile with integrated BE Secure Overhead Detection System. The BE Secure system utilizes time-of-flight measurement principles (TOF) combined with artificial intelligence (AI) algorithms to detect when two people try to enter the same compartment on a turnstile using one credential. If piggybacking is detected, the turnstile will automatically lock and refuse entry. Image courtesy of Boon Edam
Find out more at www.boonedam.com
Cobalt Robotics
Automates visitor check-in and screening
Envoy Visitors is now integrated with Cobalt Robotics’ autonomous robots, leveraging robotic technology in the visitor check-in process. Workplaces that require a visitor to register at the reception desk are greeted by a Cobalt robot. Visitors provide their information, which syncs to Envoy’s visitors log and then can be approved for entry. The visitor management solution includes instant notifications, visitor screening, digital document signing, badge printing and analytics and insights into visitor volume. Image courtesy of Cobalt Robotics
Find out more at www.cobaltrobotics.com
DITEK
Protects fire alarm systems from electrical surges
 The DTK-120X12 from DITEK is an electrical surge protection solution for fire alarm systems. Combining protection for 120V system power with protection for up to 12 low-voltage circuits, the DTK-120X12 can help eliminate damage caused by electrical surge events. The modular plug-in design aims to simplify installation & replacement of surge protection modules. The DTK-120X12 base is designed to be wall mounted and hardwired and includes the 120VAC power surge protection unit with dry contacts for remote monitoring of surge protection status. The 120VAC module also has LEDs for visual confirmation of status, as well as a loud audible alarm that sounds if protection has been compromised. Up to six compatible low voltage protection modules can be mounted to the base to protect up to 12 SLC, NAC, IDC, PIV and dialer circuit pairs. Image courtesy of DITEK
The DTK-120X12 from DITEK is an electrical surge protection solution for fire alarm systems. Combining protection for 120V system power with protection for up to 12 low-voltage circuits, the DTK-120X12 can help eliminate damage caused by electrical surge events. The modular plug-in design aims to simplify installation & replacement of surge protection modules. The DTK-120X12 base is designed to be wall mounted and hardwired and includes the 120VAC power surge protection unit with dry contacts for remote monitoring of surge protection status. The 120VAC module also has LEDs for visual confirmation of status, as well as a loud audible alarm that sounds if protection has been compromised. Up to six compatible low voltage protection modules can be mounted to the base to protect up to 12 SLC, NAC, IDC, PIV and dialer circuit pairs. Image courtesy of DITEK
Find out more at www.diteksurgeprotection.com
DoorKing
Allows for video calls in entry system
DoorKing’s model 2112 eVolve, a video telephone entry system for residential applications, is a cloud-based system that operates on an internet or cellular connection. The companion DoorKing apps are available for Android and iOS cellular phones and provide video calling and relay control, programming, event logging and more for system administrators. The 2112 model can control up to three entry points and features broadcast calling, which allows up to four phones to ring simultaneously when the call button is pushed. Image courtesy of DoorKing
Find out more at www.doorking.com
Dortronics
Controls doors to support security mantraps

Dortronic’s 48900 Door Interlock Controllers accommodate mantraps with up to nine doors. The controller is a one-board solution that gives the installer control of all operating and configuration options without complex software. The solution is suitable for air locks or security mantraps with two to nine doors that are locked or unlocked. This controller has outputs for traffic lights and door violation alarms and provides three individual timing sequences. A number of access control systems can be used with the 48900 series controllers. The 48900 controller can be paired with a four-, six- or 10-amp UL 294 power supply that includes a fire alarm connection for emergency egress and can provide power to operate maglocks, electric strikes and traffic lights. The controller is also available without the power supply & enclosure for connection to an existing 12-24VDC power source. Image courtesy of Dortronics
Find out more at www.dortronics.com
Elite Interactive Solutions
Leverages AI and security professionals to monitor facilities
Elite Interactive Solutions’ Remote Guarding Intelligence creates the ability to monitor a customer site in real time while streaming processes and communications across organizations. Elite Interactive Solutions Remote Guarding Intelligence employs military-derived AI technology that detects people on properties and sends an alert to command and monitoring centers where security professionals view what is happening. If a suspicious person or activity is observed, personnel address the individual(s) over a two-way security audio system, alerting them they are being watched and requesting them to leave immediately. If the activity indicates that an imminent crime or threat is occurring, police are immediately notified to respond. Image courtesy of Elite Interactive Solutions
Find out more at www.eliteinteractivesolutions.com
HID
Connects employee badges to Apple Wallet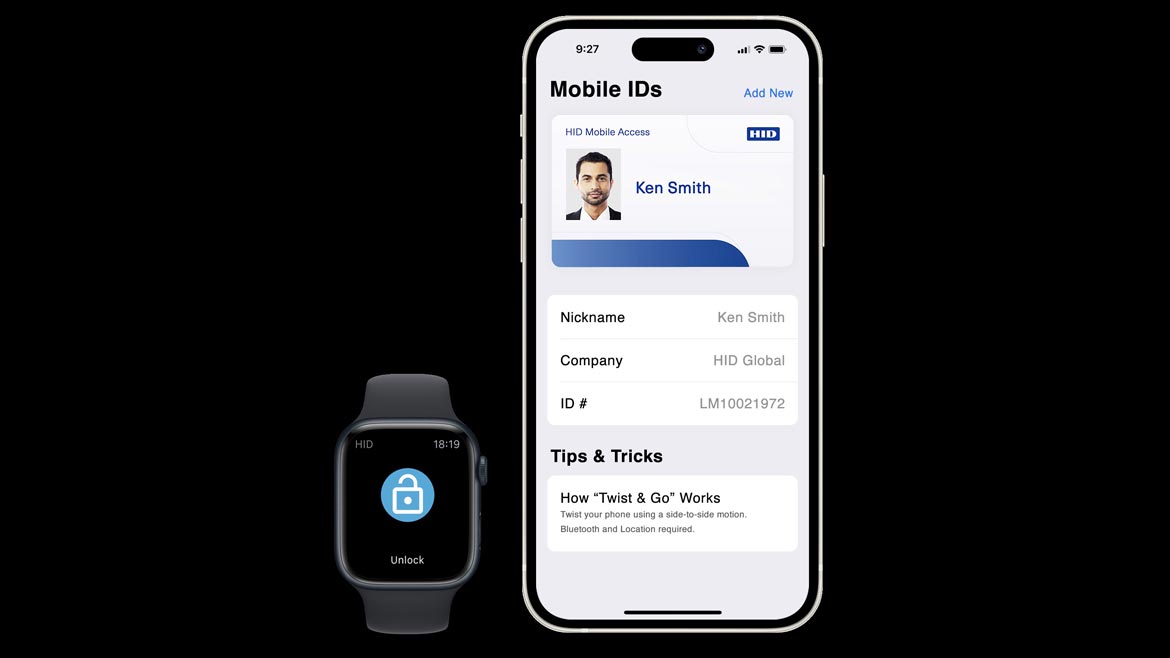
HID Mobile Access enables digital credentials on mobile devices to securely authenticate to readers for physical access control and other extended access applications. With HID’s employee badge in Apple Wallet, users can access office doors, elevators, turnstiles and building amenities using their iPhone or Apple Watch. It integrates into existing access control systems and is supported by Seos, HID’s credential technology, to create a mobile access experience. Image courtesy of HID
Find out more at www.hidglobal.com
i-PRO
Surveils facilities with built-in analytics
i-PRO’s WV-X86531 multi-directional and pan-tilt-zoom (PTZ) camera is a small and light outdoor-rated multi-PTZ with support for up to five sensors total — four multi-sensor and the PTZ. Pre-installed with AI edge-based analytics, the camera can support four applications on the multi-sensor array and two unique applications on the PTZ. AI auto-tracking ensures the PTZ doesn’t lose lock on the subject when the camera recognizes an object. The WV- X86531 features cybersecurity and vandal resistance. Image courtesy of i-PRO
Find out more at www.i-pro.com
Iris ID
Integrates biometrics into travel identification & access control
The iCAM D2000 from Iris ID is an iris and face identification system that uses biometrics to provide images for enrollment and identification for travel and access solutions. The iCAM D2000 helps travelers navigate airport checkpoints and can integrate with other identity authentication systems. Solution functions include multimodal (iris & face) simultaneous capture, user height accommodation and mask detection, among others. Image courtesy of Iris ID
Find out more at www.irisid.com
Morse Watchmans
Tracks key usage within an enterprise
Morse Watchmans’ KeyWatcher Touch system is a key control and asset management solution for organizations of all sizes. This helps security professionals control and track usage of keys or personal assets. With a 7” touchscreen and patented SmartKey system with KeyAnywhere technology, authorized individuals can withdraw and return a key securely to key cabinets located within an enterprise. Administrators can locate which KeyWatcher Touch a specific key is in, or determine who has it out, with the KeyFind feature. The system can also enable security management to notify a user via email when a key becomes overdue. The Generation 3 CPU aims to improve performance, quicken the user interface, and improve synchronization times. Image courtesy of Morse Watchmans
Find out more at www.morsewatchmans.com
Ontic
Takes a proactive approach to threat management
Ontic’s corporate security solution aims to support proactive threat management and risk mitigation, helping organizations protect people, facilities and assets at a number of locations. Threat monitoring tools, system integrations and a single source for data management and reporting allow threats to be identified before they turn critical. With real-time signals, continuous visibility of behavioral indicators, coordinated interventions and responses, and informed risk and threat assessments, the Ontic platform aims to help organizations recalibrate and shift to a strategic approach to threat management and risk mitigation. Image courtesy of Ontic
Find out more at www.ontic.co
RGB Spectrum
Enables a range of surveillance displays
 RGB Spectrum’s series of new video processing technology & enhancements aims to deliver visual information from source to destination: from a video wall in an operation center, to a monitor in an office across a campus or a cell phone anywhere in the world. It allows personnel to collect data from sources located anywhere, view that information on available displays, and share resulting intelligence throughout an enterprise environment. The Zio platform is the backbone of RGB Spectrum’s decision support system. Zio provides real-time audio and video distribution across packet-based networks, including local area networks (LANs), wide-area networks (WANs), virtual private networks (VPNs), and mobile networks. Images courtesy of RGB Spectrum
RGB Spectrum’s series of new video processing technology & enhancements aims to deliver visual information from source to destination: from a video wall in an operation center, to a monitor in an office across a campus or a cell phone anywhere in the world. It allows personnel to collect data from sources located anywhere, view that information on available displays, and share resulting intelligence throughout an enterprise environment. The Zio platform is the backbone of RGB Spectrum’s decision support system. Zio provides real-time audio and video distribution across packet-based networks, including local area networks (LANs), wide-area networks (WANs), virtual private networks (VPNs), and mobile networks. Images courtesy of RGB Spectrum
Find out more at www.rgb.com
RightCrowd
Automates physical access control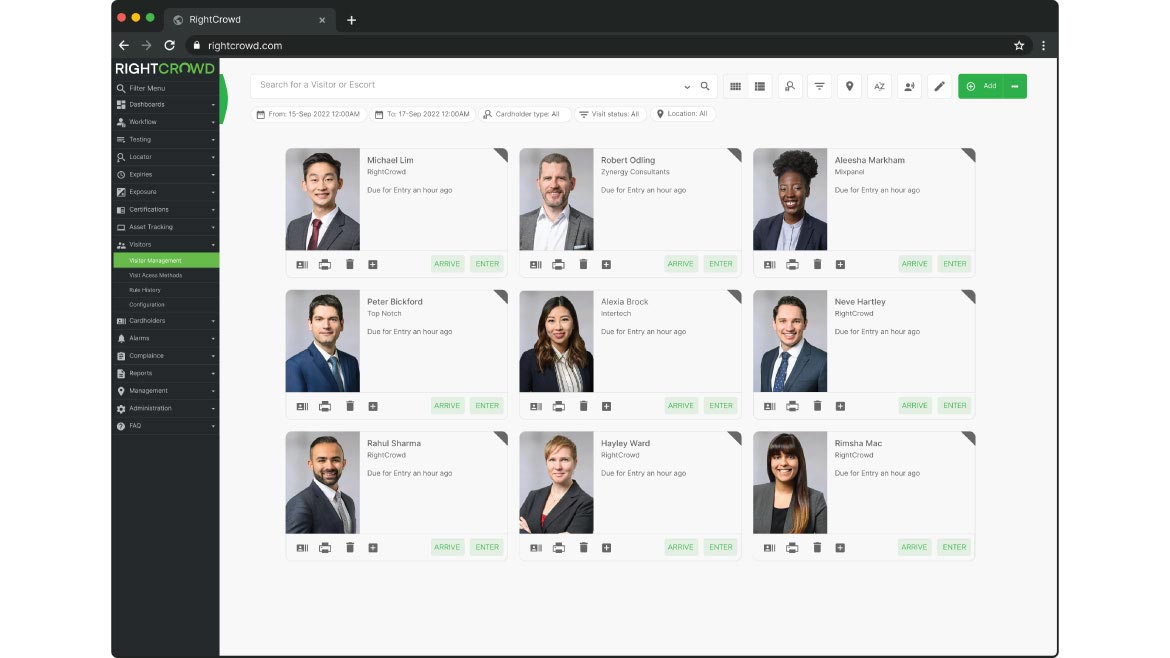
RightCrowd Workforce Access is a physical identity and access management (PIAM) solution that automates the physical access control processes for employees, visitors and contractors across their access lifecycle. The solution adds a layer of intelligent automation to extend access management capability. RightCrowd Workforce Access helps automate access control processes and workflows, enables self-service and implements attribute-based access control (ABAC) rules in accordance with an organization’s security policies, safety rules and compliance requirements while keeping cardholder data up-to-date. Image courtesy of RightCrowd
Find out more at www.rightcrowd.com
Shooter Detection Systems
Detects gunshots in indoor environments
Shooter Detection Systems’ (SDS’) Active Shooter Intelligence technology is engineered for precision, performance and saving lives. SDS’ Indoor Gunshot Detection solutions aims to help end-users detect a gunshot and respond quickly. SDS’ indoor gunshot detection system utilizes dual-mode acoustic and infrared detection technology that detects and reports shots fired in under a second, alerting building occupants while also pushing incident data to 911. Image courtesy of Shooter Detection Systems
Find out more at www.shooterdetectionsystems.com
Sielox
Applies intelligence to access management processes
Sielox’s Pinnacle 11 aims to provide innate intelligence that allows access control users to leverage preemptive data and notifications for a comprehensive range of applications, including privileged access levels; contractor and contingent worker management; emergency access management, including lockdowns and mustering; occupancy management; compliance/audit management; workforce management time and attendance; insider threat detection and risk mitigation; health management and contact tracing; and more. Pinnacle 11 is compatible with a number of access products and supports Windows 11, time zone schedules and holidays, and email notification. Image courtesy of Sielox
Find out more at www.sielox.com
Vector Flow
Helps automate enterprise identity management
Vector Flow’s Physical Workforce Identity Suite helps automate the physical security identity lifecycle. The solution leverages AI technology to automate identity management tasks such as on- and off-boarding of an identity into physical security infrastructure, badging and credentialing, physical access management, access audits and compliance. The AI-enabled software uses learning algorithms to identify and address security gaps and also delivers recommendations for security improvements and user tasks. The Physical Workforce Identity Suite leverages its tools set such as Design Studio to manage changes in the application; Playbooks to automate rules, workflows, schedules and tasks; and Recommendation Engine to precisely automate user tasks which otherwise would be done manually. Image courtesy of Vector Flow
Find out more at www.vectorflow.com
Viakoo
Automates password compliance of physical security and IoT devices
The latest version of Viakoo’s Device Password Manager automates password rotation and scheduling, verification of password strength, coordination with VMS and other applications, and adherence of password policies at scale for thousands of devices. The solution aims to help security leaders mitigate the challenges associated with weak password management strategies. Image courtesy of Viakoo
Find out more at www.viakoo.com
Vintra
Simplifies manual security processes with monitoring & alerts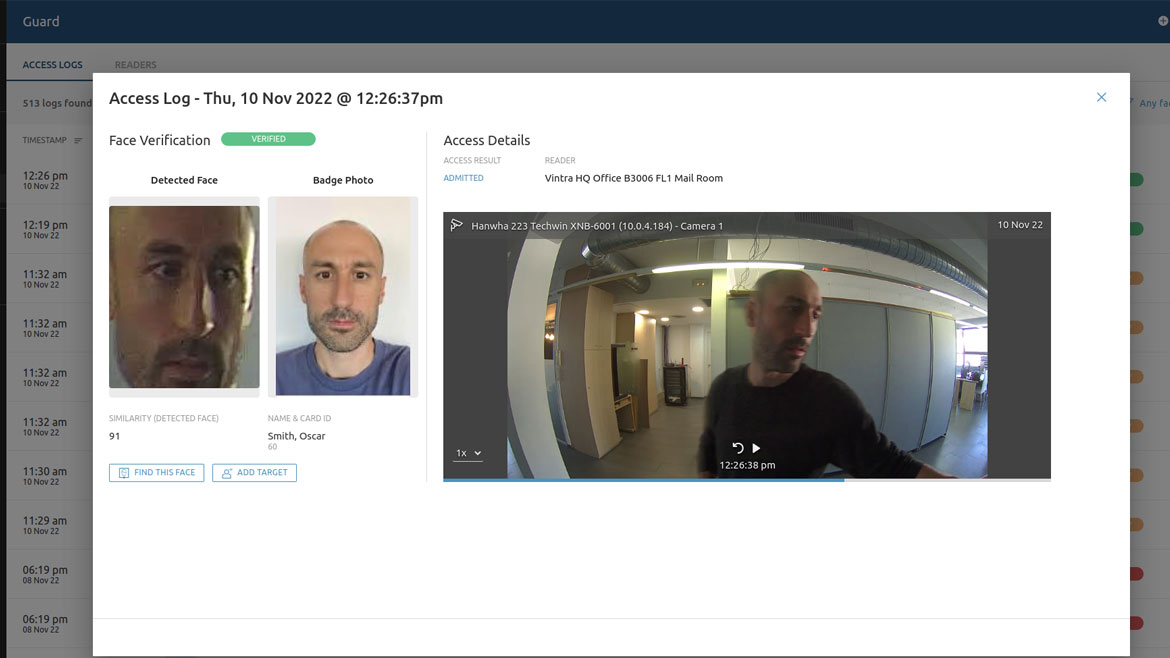
Vintra Guard, available as an additional module for Vintra Prevent, can enhance real-time monitoring and enterprise alerting by incorporating video-based identity verification for access control management. Initially integrated with the C•CURE 9000 Security + Event Management System, Vintra Guard automates two-factor identity verification for C•CURE users, incorporating video analytics into the access control system to help detect unauthorized access across a campus facility. The solution can review access events at a given point of entry, using facial recognition to verify the identity of the person that used each credential in order to find any unauthorized credential usage. If a badge is used by an individual that is not the actual credential holder, an alert will be generated, available within the Vintra Fortify platform or sent to a VMS platform. Image courtesy of Vintra
Find out more at www.vintra.io





